Table of Contents
Configuration of fault tolerance switching between 2 ISP and NAT for Internal network on the Juniper SRX 220H cluster and Cisco 1941
Introduction.
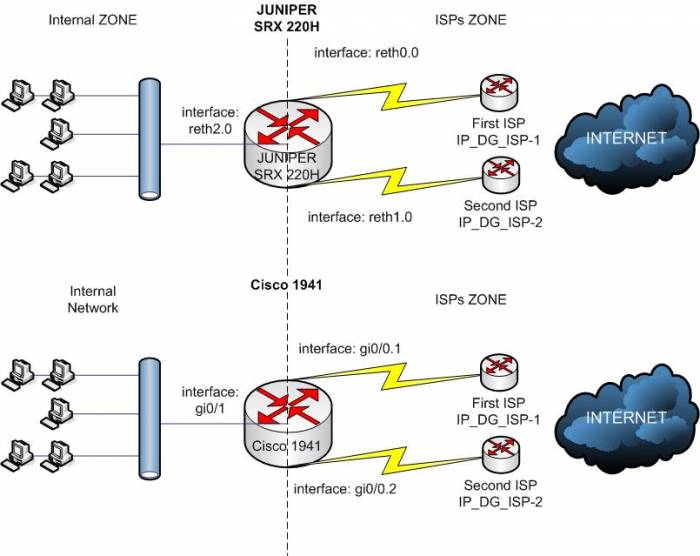
We have 2 ISP and internal network with INTERNAL_NET/24.
Task:
configure on the Juniper SRX 220H and Cisco 1941 NAT for internal network and fault tolerance switching between ISPs.
Solution for Juniper SRX 220H Cluster.
1. Requirements: JunOs verion 11 or above
2. Configure two security zones on the Juniper:
{primary:node1}[edit]
set security zones security-zone ISPs interfaces reth0.0
set security zones security-zone ISPs interfaces reth1.0
set security zones security-zone Internal interfaces reth2.0
set security zones security-zone Internal address-book address INTERNAL_NET INTERNAL_NET/24
3. Configure security policies
{primary:node1}[edit]
set security policies from zone Internal to zone ISPs policy Internal_to_ISPs match source-address INTERNAL_NET
set security policies from zone Internal to zone ISPs policy Internal_to_ISPs match destination-address any
set security policies from zone Internal to zone ISPs policy Internal_to_ISPs match application any
set security policies from zone Internal to zone ISPs policy Internal_to_ISPs then permit
4. Configure static routing.
{primary:node1}[edit]
set routing-options static route 0.0.0.0/0 next-hop IP_DG_ISP-1
set routing-options static route 0.0.0.0/0 qualified-next-hop IP_DG_ISP-2 preference 100
5. Configure monitoring of ISPs. We will monitor default gateways for this example.
{primary:node1}[edit]
set services rpm probe First_ISP-Probe test First_ISP_GW target address IP_DG_ISP-1
set services rpm probe First_ISP-Probe test First_ISP_GW probe-count 10
set services rpm probe First_ISP-Probe test First_ISP_GW probe-interval 5
set services rpm probe First_ISP-Probe test First_ISP_GW test-interval 10
set services rpm probe First_ISP-Probe test First_ISP_GW thresholds successive-loss 10
set services rpm probe First_ISP-Probe test First_ISP_GW thresholds total-loss 5
set services rpm probe First_ISP-Probe test First_ISP_GW destination-interface reth0.0
set services rpm probe First_ISP-Probe test First_ISP_GW next-hop IP_DG_ISP-1
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW target address IP_DG_ISP-2
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW probe-count 10
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW probe-interval 5
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW test-interval 10
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW thresholds successive-loss 10
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW thresholds total-loss 5
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW destination-interface reth1.0
set services rpm probe Second_ISP-Probe test Second_ISP-Probe_GW next-hop IP_DG_ISP-2
set services ip-monitoring policy First_ISP-Tr match rpm-probe First_ISP-Probe
set services ip-monitoring policy First_ISP-Tr then preferred-route route 0.0.0.0/0 next-hop IP_DG_ISP-2
set services ip-monitoring policy Second_ISP-tr match rpm-probe Second_ISP-Probe
set services ip-monitoring policy Second_ISP-tr then preferred-route route 0.0.0.0/0 next-hop IP_DG_ISP-1
6. Configure NAT
{primary:node1}[edit]
set security nat source rule-set From_Internal_to_ISPs from zone Internal
set security nat source rule-set From_Internal_to_ISPs to zone ISPs
set security nat source rule-set From_Internal_to_ISPs rule NAT_INTERNAL match source-address INTERNAL_NET/24
set security nat source rule-set From_Internal_to_ISPs rule NAT_INTERNAL then source-nat interface
7. Commit
{primary:node1}[edit]
commit
Solution for Cisco 1941.
1. Requirements: cisco ios version 15 with DATA licence
2. At first we need to configure dotq1 on first interface because we have only two physical interface on the cisco 1941 (without extended modules).Also we will need a switch with dotq1 support. Both ISPs should be connected to a switch.
conf t int gi 0/0.1 description First_Provider encapsulation dot1Q 1 exit int gi 0/0.2 description Second_Provider encapsulation dot1Q 2 end
Don't forget to configure IP addresses on above mention interfaces
conf t int gi 0/1 descriptions Internal Network exit
3. Configure monitoring
conf t ip sla 1 icmp-echo IP_DG_ISP-1 source-interface GigabitEthernet0/0.1 timeout 2000 threshold 2000 frequency 3 exit ip sla schedule 1 life forever start-time now ip sla 2 icmp-echo IP_DG_ISP-2 source-interface GigabitEthernet0/0.2 timeout 2000 threshold 2000 frequency 3 exit ip sla schedule 2 life forever start-time now end
4. Configure track
4. Конфигурация track
conf t track 1 rtr 1 reachability delay down 60 up 30 exit track 2 rtr 2 reachability delay down 60 up 30 end
5. Configure routing.
conf t ip route 0.0.0.0 0.0.0.0 IP_DG_ISP-1 track 1 ip route 0.0.0.0 0.0.0.0 IP_DG_ISP-2 10 track 2 end
6. Configure NAT
conf t int gi 0/0.1 ip nat outside exit int gi 0/0.2 ip nat outside exit int gi 0/1 ip nat inside exit ip access-list 99 permit INTERNAL_NET 0.0.0.255 ip nat inside ip nat inside source list 99 interface gigabitEthernet 0/0.1 overload ip nat inside ip nat inside source list 99 interface gigabitEthernet 0/0.2 overload end
7. Create scripts for cleaning of NAT-table and reporting to syslog.
conf t scheduler allocate 20000 1000 event manager directory user policy flash:/tcl event manager applet ISP_1_DOWN event syslog pattern "%TRACKING-5-STATE.*1 rtr 1 reachability Up->Down" action 1.0 cli command "enable" action 1.1 cli command "clear ip nat translation *" exit event manager applet ISP_1_UP event syslog pattern "%TRACKING-5-STATE.*1 rtr 1 reachability Down->Up" action 1.0 cli command "enable" action 1.1 cli command "clear ip nat translation *" exit event manager applet ISP_2_DOWN event syslog pattern "%TRACKING-5-STATE.*2 rtr 2 reachability Up->Down" action 1.0 cli command "enable" action 1.1 cli command "clear ip nat translation *" exit event manager applet ISP_2_UP event syslog pattern "%TRACKING-5-STATE.*2 rtr 2 reachability Down->Up" action 1.0 cli command "enable" action 1.1 cli command "clear ip nat translation *" end
8. Save configuration
wr
About author
Profile of the author